To enter the spaceship security system, the astromechanical droid R2-D2 uses a secret cryptographic algorithm, one step of which solves the following problem:
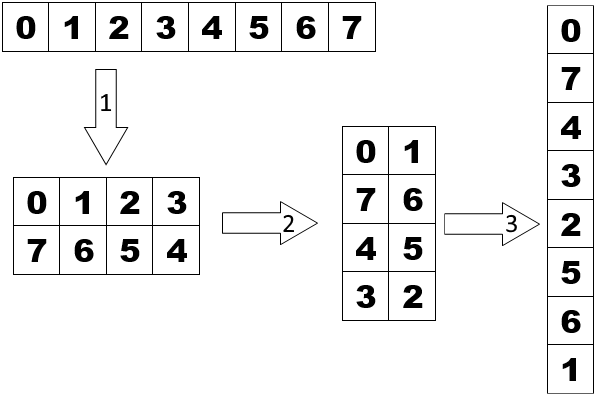
Consider a thin paper strip with n = 2k cells located in one row. The cells are numbered 0 through n - 1. Fold the strip in half, the right half under the left one, so that the cell numbered 2k - 1 - j will be above the cell numbered 2k - 1 + j - 1 for all j from 1 to 2k - 1. Then fold the resulting strip, which has how length 2k - 1, again and again in the same way until the length of the strip is one. In the resulting folded strip, the cells are placed above each other in some order. Let the sequence a0, a1, ..., an - 1 be the numbers of the cells from top to bottom.
When the droid connects to the spaceship system, it is given an integer n, and after that, it is asked several queries to get verified. Each query is a segment [l, r] (0 ≤ l ≤ r < n) for which the droid must compute the following expression, in which operations + and  alternate:
alternate:
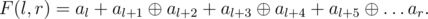
 if l is even, and operation
if l is even, and operation  has higher priority than + otherwise. If the droid doesn't answer correctly these queries in one second, he is revealed.
has higher priority than + otherwise. If the droid doesn't answer correctly these queries in one second, he is revealed.R2-D2 argued with C-3PO that the latter couldn't solve this problem. C-3PO is a protocol droid, it knows six million forms of communication, but nothing about cryptography. Help him to solve the problem in order to surprise R2-D2.
In order to emulate a security system, R2-D2 suggested an algorithm for choosing the segments [l, r]. He also suggested to check only the results of hashing F(l, r), but not the values F(l, r) themselves. Let the queries be numbered 0 through m - 1. Then these values are computed as follows:
-
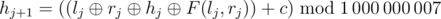 ;
; -
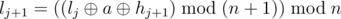 ;
; -
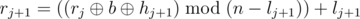 .
.
Here, h is the value of the hash function, and h0 = 0. Your task is to compute the final hash value hm.
The first line of input contains an integer k (0 ≤ k ≤ 30).
The second line contains three integers m, l0, r0: the number of queries and the bounds of the initial query (1 ≤ m ≤ 107, 0 ≤ l0 ≤ r0 < n).
The third line contains three integers a, b and c: the parameters of the generating algorithm (0 ≤ a, b, c < 230).
Print one integer hm: the value of the hash function after processing all queries.
3
1 2 6
3 4 5
7
3
709193 4 5
273035200 65685838 991992535
156951996
Operation  means exclusive or.
means exclusive or.
The results of operations with higher priority must be computed earlier. Operations with the same priority must be processed in the order from left to right.
A strip of length 23 = 8 folds like in the picture.
| Name |
|---|




